
Imagine someone reading your diary, rummaging through your medicine cabinet, or taking a peek at your bank balances. Unsettling.
Now imagine that a cybercriminal has stolen your Social Security number, bank account access, and medical records and is selling your private data on the online black market. Maybe someone has already opened credit card or loan accounts in your name, drained your bank account, or trashed your credit. Alarming!
Weak Passwords Spell Disaster
We’re storing more and more of our personally identifiable information (PII) online. These are private details we seldom share with others, face to face, and only with those who need to know.
To protect our PII from hackers and criminals, we restrict access by setting passwords.
But those passwords are only as secure as we make them.
Creating and remembering safe passwords can be time-consuming and tedious. It’s easier to use your pet’s name, your birthday, or your kids’ names than a long, complicated password that contains at least one numeral, one symbol and includes both upper- and lowercase letters. Equally frustrating, many websites have unique requirements for the characters permitted and character length.
But as annoying as password security measures can be, they’re based on mathematics and exist to protect you.
Let’s examine why ignoring these rules can enable a hacker to crack your password in seconds.
Protecting Your Password: Behind the Scenes
As an account user, logging in usually happens quickly and feels seamless. But behind the scenes, multiple activities are synchronized to prevent hackers from discovering your password.
Ever wonder why you can’t retrieve your password when you’ve forgotten it—but instead have to reset it completely? When you create a new password, responsible companies don’t store the plain-text version of your password because anyone with access to the password database could retrieve — and use or sell — all of the stored passwords. So instead, they encrypt your password and save that.
But storing an encrypted version of user passwords does not provide adequate protection because hackers — or crackers, as they call themselves — have access to meticulously compiled tables, known as rainbow tables, containing millions of pairs of encrypted and non-encrypted passwords.
Crackers with access to your encrypted password could search rainbow tables for a match to locate your unencrypted password.
To defeat or reduce the effectiveness of rainbow tables, responsible companies generate and append a unique plain-text string of characters to each password. The series of randomly generated extra characters is called a “salt.” The combined string of characters (your password plus the salt) is encrypted. Adding the salt to your password before encrypting it changes the encrypted result. After salting, your encrypted password will no longer match the encrypted value in a rainbow table, thus limiting the effectiveness of rainbow tables.
This article explains salts in more detail, but here is what a successful login looks like when your password contains a salt:
- Type in your user ID and password, then click the login button.
- Company software locates your user ID in a database and retrieves the database’s associated record of the salt (that randomly generated additional text string). It also retrieves your hash (encrypted value).
- The software appends the salt to the password you’ve entered.
- It encrypts the combined password and salt.
- Finally, it compares the result with the stored hash.
- Do they match? If so, you’re in!

Why Create Sophisticated Passwords?
With all this protection, why is it still so easy for hackers to crack passwords?
1. Computers are getting faster every year. A lot faster.
Each year, computer processors reach new speeds that defy imagination; since the advent of the microchip, processing speed has doubled roughly every 12 months. Hackers tap the ever-increasing power of computer processors to crack passwords faster every year.
Today, even amateur hackers can assemble machines capable of attempting (guessing) a staggering 327 billion passwords each second. Anyone with $5,000 can form a cluster of high-speed graphics processing units (GPUs) that operate in sync to produce incredible processing power with speeds of 327 GHz/second. In the wrong hands, such a device is a formidable weapon.
2. Convenience often trumps safety.
Computer speed isn’t the only factor in rapid-fire password cracking. Many instances of password cracking are preventable, but users who choose weak passwords open the door to security breaches. Most people view passwords as a nuisance—a necessary evil to log into an account. And with all the information that we keep online, you likely need more passwords than you can remember.
Many of us already know never to use easily discoverable information for our passwords, such as:
- your birthday, first or last name, children’s names, or anniversaries
- memorable number patterns, like 1234 or 4321
- a single character type (all upper or lowercase, all numerals, or all letters).
Many people still expose themselves to unnecessary risk by creating passwords with common and easy-to-remember passwords. And those who use the same password across multiple accounts are at even greater risk because criminals who discover that one password gain unrestricted access to every account that uses that password.
Use the free tool at haveibeenpwned to determine if your email address is associated with any known data breaches. If you’re like most of us, criminals are already selling passwords you’ve used on the black market, along with any personal information you divulged to breached websites.
3. Underestimating the risks.
Most of us don’t understand how quickly a cracker could discover our passwords and access our online information. And if we’ve managed to skate along with an insecure password for a while without being hacked, it is easy to believe, “It won’t happen to me.” Unfortunately, online security isn’t top-of-mind until after we’ve become victims of identity theft.
Password Cracking: A Real-Life Example
How easy is it to crack your password? Let’s look at some examples using the GPU calculations in this article. We’ll stick to combinations of uppercase letters (26), lowercase letters (26), the numerals 0-9 (10), and the five symbols { #, @, $, ! % }. Here we go.
Joe Smith is tired of having to click “Forgot Password?” every time he tries to sign in to his bank account. So he changes it to something he knows he will remember. Joe is a stamp collector. His new password will be the word stamps. Easy? Yes! Dangerous? Absolutely!
Joe’s new password contains six lowercase letters. It is one of a possible 308,915,776 passwords, based on the total available lowercase letters (26), to the power of the length of the password, which is six characters.
That sounds like a lot of passwords that would take a long time to crack, right? You’d think so, except even the most basic password-cracking software can generate up to 3.2 million password guesses in one second, and the GPU cluster can crack that password in a fraction of a second.
So let’s help Joe out and make his password a little more secure by adding numbers: st4mps. His password is now one of a possible 2,176,782,336 (26 possible lowercase letters plus ten possible numerals, for a total of 36 characters, to the power of 6: the length of his password).
Now let’s help him a little more by capitalizing some of the letters and adding symbols: $T4mp$. Joe’s password is now one of a possible 90,458,382,169.
Let’s compare these passwords, assuming the cracker uses a low-tech system that can guess 3.2 million passwords per second. It will take 96 seconds (about a minute and a half ) to crack stamps, 680 seconds (roughly 11 minutes) to break st4mps, and 28,268 seconds (more than 7 hours) to crack $T4mp$. But someone with a GPU cluster can still crack the most challenging version, $T4mp$, in less than a second.
Increasing the number of characters in your tool chest is helpful, but Joe is still not safe (yet) from anyone willing to invest $5,000 in a strong password cracking system. What else can he do?
Long passwords are safer.
Ever wonder why most websites require a minimum of 8 characters? The reason is simple: the longer your password, the more time needed to crack it.
Watch what happens as we extend the length of the password.
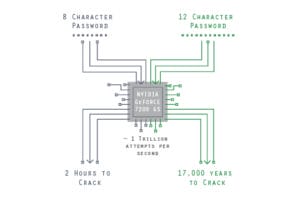
As the graphic below illustrates, cybercriminals using powerful and relatively affordable current technology can crack an 8-character password in about two hours. Still, they will need 17,000 years to exhaust every option for a 12-character password. By adding only four more characters, you can keep them busy for a very long time.
How to Create a Hardened Password
Are you ready to test your passwords and create new ones to protect your data? Try this password tester to see how quickly your accounts could be hacked and get suggestions on generating better passwords. Remember:
- Never use information that’s easy for others to guess
- Always use a combination of upper and lowercase letters, numbers, and symbols
- Longer passwords are more robust. A password 20 characters long (41 characters to the 20th power) is exponentially stronger than one that’s only six characters long (41 characters to the 6th).
No matter how strong your passwords are this year, they will be easier to crack next year—and even easier the year after that. Stick to long passwords with various cases, characters, and numbers to ensure robust online security for years to come.
And whenever a company offers two-factor authentication (2FA), use it. 2FA requires the use of two separate verifications — for instance, asking you to enter a temporary code texted to you, or your childhood best friend’s name, in addition to your username and password. While it is becoming increasingly trivial for hackers to crack your password, guessing a code sent to a device the hacker can’t access is far more time-consuming.

